Do you hope to find 'cryptography research paper'? You will find all the information on this section.
Table of contents
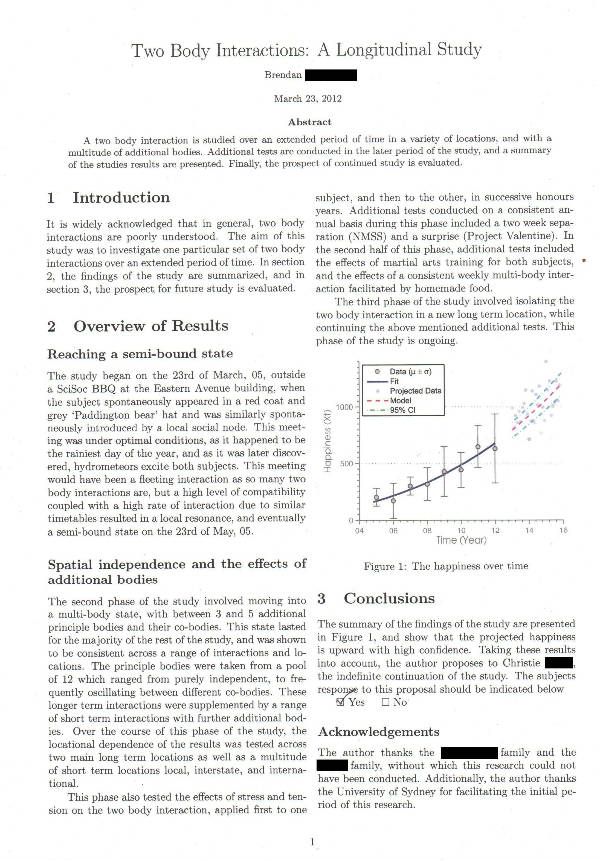
- Cryptography research paper in 2021
- Msr crypto group
- Cryptography research inc
- Cryptography research papers pdf
- Literature review on cryptography
- Cryptography research papers 2019
- Cryptography research topics 2020
- Encryption for dummies pdf
Cryptography research paper in 2021
 This image illustrates cryptography research paper.
This image illustrates cryptography research paper.
Msr crypto group
 This image demonstrates Msr crypto group.
This image demonstrates Msr crypto group.
Cryptography research inc
 This picture shows Cryptography research inc.
This picture shows Cryptography research inc.
Cryptography research papers pdf
 This image demonstrates Cryptography research papers pdf.
This image demonstrates Cryptography research papers pdf.
Literature review on cryptography
 This picture illustrates Literature review on cryptography.
This picture illustrates Literature review on cryptography.
Cryptography research papers 2019
 This picture illustrates Cryptography research papers 2019.
This picture illustrates Cryptography research papers 2019.
Cryptography research topics 2020
 This picture demonstrates Cryptography research topics 2020.
This picture demonstrates Cryptography research topics 2020.
Encryption for dummies pdf
 This image representes Encryption for dummies pdf.
This image representes Encryption for dummies pdf.
What is the definition of a cryptography technique?
Cryptography can be defined as techniques that cipher data, depending on specific algorithms that make the data unreadable to the human eye unless decrypted by algorithms that are predefined by the sender. … … … Content may be subject to copyright.
Which is a recent research paper in cryptography?
ABSTRACT Recent papers have considered the use of linear codes with structure (cyclic, dyadic) to reduce the public key size of code-based public key encryption schemes (McEliece, Niederreiter). We review here the security of those cryptosystems and examine
What are the Ty PES of cryptography algorithms?
This research focused on different ty pes of cryptography algorithms that are nformation Security, Encryption, Decryption. shooting, revelation, perturbation and adjustment of computer network sources. Enhancing the privacy, to improve new ways that are resistant to most kinds of attacks if not all [1].
What are the different types of cryptography algorithms?
This research focused on different types of cryptography algorithms that are existing, like AES, DES, TDES, DSA, RSA, ECC, EEE and CR4…etc. … … … … Content may be subject to copyright. Content may be subject to copyright. Content may be subject to copyright.
Last Update: Oct 2021